We improved our client’s cloud security by creating a Zero Trust network for Windows 365 virtual machines with Microsoft Entra Private Access (Pre GA version). Our client could enhance their safe and seamless access to their production applications and private network.
Our client
Undisclosed
The challenge
The client’s challenge was securing thousands of Windows 365 virtual machines from unauthorized access to their internal network resources, especially the critical applications they weren’t supposed to access. The client initially considered using Microsoft ExpressRoute to create a shared network between the virtual machines and the internal applications. Still, this solution didn’t meet their security goal of isolating the virtual machines from other parts of the network.
The client decided to use Microsoft Entra Private Access. This new tool enables cloud computers to communicate with internal applications by creating a tunnel that only allows access to registered and authorized applications. However, this tool wasn’t in GA yet and had little documentation or examples, so the project was challenging and required daily collaboration with the client and Microsoft.
How we helped
Our project had three main objectives:
- Show that Microsoft Entra Private Access could be used to connect Windows 365 virtual machines and various internal applications with different network protocols and latency needs.
- Make sure that Microsoft Entra Private Access fulfills all necessary security requirements, such as per-application access control and zero-trust network access.
- Build an MVP solution based on the client’s non-production environment requirements.
We agreed the best approach would be to gather and document all the client’s security requirements and verify that Microsoft Entra Private Access could address these. Once we were confident that Microsoft Entra Private Access could satisfy all security demands, we would conduct a short POC to confirm that connectivity to the internal network could be achieved and that the different kinds of applications the client had would all function across the tunnel which Microsoft Entra Private Access would form. Finally, once the MVP was set up, we could validate the security of the service and ensure that any increased latency would be minimal.
Microsoft End Customer Investment Fund (ECIF)
This project leveraged the Microsoft End Customer Investment Fund (ECIF), which provided funding that substantially reduced deployment costs for our client. The A-CX team independently executed every aspect of the Azure Entra PA Zero Trust deployment – without the need for Microsoft resources – showcasing the depth of our technical expertise and commitment to delivering measurable value. Overall, this ECIF-backed approach streamlined the project timeline while ensuring a cost-effective, high-impact security solution for our client.
Understanding Microsoft Entra Private Access
Microsoft Entra Private Access enables cloud computers to communicate with internal applications by creating a tunnel from the computers to the network on the premises. The Entra Global Secure Access Client, or GSA client, sets up the tunnel by intercepting traffic on the installed machine and deciding if it needs to go to the internal network. The tunnel goes from the GSA client to an Entra Private Access Connector on the premises, which ends the tunnel and connects it to the application on the premises.
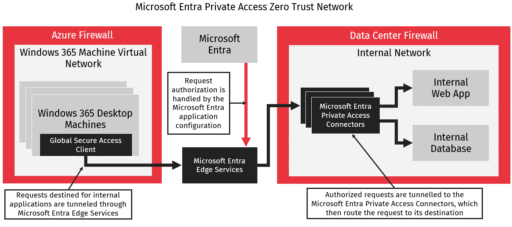
Microsoft Entra Private Access secures applications and keeps them and isolates applications by requiring registration in Microsoft Entra (previously Active Directory). Only registered applications can be connected to through the Entra Private Access tunnel. Further, registered applications can have users and groups assigned to them, and only those assigned users or users in the assigned groups, can access the application through the tunnel.
Discussing Security Concerns
Our client’s two biggest security concerns were ensuring that only certain users would be able to access certain applications across the network and that unencrypted application requests would be encrypted on the connection to the internal network. We worked closely with the Microsoft Entra development team to ensure that both of these security concerns would be sufficiently addressed.
To ensure that only certain users could access certain applications, we first built a proof of concept on our own internal network and validated how Microsoft Entra Private Access handled authentication and authorization. We verified that Microsoft Entra Private Access could be used to restrict user access to certain applications and that applications were further restricted to certain FQDNs or IP addresses. The client’s applications were typically connected via FQDN, so we confirmed that Microsoft Entra Private Access would restrict user access the way the client needed.
We had an extensive discussion with Microsoft about how the encrypted connection via the Microsoft Entra Edge Services operates. We learned that the GSA client establishes a secure connection that routes requests through it. This connection is not disrupted internally, so messages transmitted through the connection are protected and stay protected until the connection terminates at the Microsoft Entra Private Access Connectors within the client’s network.
Demonstrating the Solution
Once we understood the security concerns and were confident that Microsoft Entra Private Access would be able to address these concerns, we began constructing a POC to verify that Microsoft Entra Private Access would function correctly in the customer environment. The POC would be made up of four separate steps:
- Deploying Entra Private Access Connector into the client’s internal non-production network.
- Installing the Entra Global Secure Access Client on a test Windows 365 virtual machine.
- Adding the Entra Private Access Connectors and test applications to Microsoft Entra.
- Testing the latency and security of Entra Private Access.
Establishing Internal Endpoints
The first step was to deploy the Microsoft Entra Private Access Connectors. These connectors serve as the endpoints into the private network for the Windows 365 machines. The connectors establish outbound connections to the Microsoft Entra Edge Service, where they are authenticated. For initial testing purposes, we got an internal server that had network access to all the internal applications we needed to test. We then installed the Global Secure Access client on the machine and opened the firewall to allow the outbound authentication connection to the Entra Edge services. Finally, we configured the connector to authenticate itself with the Microsoft Entra Edge Service successfully.
Configuring the Windows 365 Machine
Once we had an internal connector running the next step was to deploy the Global Secure Access Client on a test Windows 365 machine. The Global Secure Access client, or GSA client, can be downloaded directly from Microsoft. Installation and configuration is straightforward, the client automatically uses the logged-in users credentials. We made some configuration changes on the Windows 365 machine to ensure the client would both correctly capture traffic and be able to connect through the firewall to the Microsoft Entra Edge services.
Updating Microsoft Entra Permissions
Finally, we had to register the applications to test in Microsoft Entra. Applications can be registered in Microsoft Entra through the Microsoft Entra Admin Center’s Global Secure Access functionality. Registered applications require a name, the list of Private Access Connectors they can be connected to from, and either the FQDNs or IPs of the application. Once the test applications were registered, we had to assign users to the applications. We created a test user group, added a set of test users to the group, and finally assigned this test group to our test applications.
Validating The Connectivity
Once we established the Microsoft Entra Private Access Connectors, deployed the GSA client and registered our applications in Microsoft Entra, we demonstrated connectivity to the client by connecting to the various test applications. Our testing showed minimal latency overhead and that the test applications did not encounter domain name resolution or network communications issues while being run over the private access tunnel.
Results
As a result of this project, our client got a minimum viable solution demonstrating the feasibility and benefits of using Microsoft Entra Private Access to connect Windows 365 clients to internal applications securely. The solution consisted of four connectors deployed in Azure, a GSA client application installed on the Windows 365 desktops, a set of test applications hosted on the client’s internal network, and a set of scripts and scenarios to validate the solution’s functionality, performance, and security.
The solution was successfully tested and validated by the client’s IT team and security auditors, who confirmed that it met the project’s requirements and expectations. The solution also provided insights and feedback for future improvements and enhancements of the Microsoft Entra service, such as better integration and automation with existing identity and access management systems, support for more protocols and platforms, and more granular control and visibility over the private access connections. The client was happy with the result of the project and planned to take the following steps to deploy it across their Windows 365 fleet when Entra PA is in the general availability phase.
Please contact us for more information about this case study or about how Microsoft Entra PA can improve your business-critical cloud security
Date
6/2024
Languages
Java
JavaScript
Frameworks
Microsoft Entra PA (Pre GA)
Microsoft Graph API
Azure Resource Manager (ARM)
Tools
Visual Studio Code
Windows 365
Cloud
Azure
Discuss your project
Great things happen when good people connect. Leave us your details, and we’ll get back to you.
By sending the information in this form, you agree to have your personal data processed according to A-CX’s Privacy policy and Cookie policy to handle the request and respond to it.